Below you will find pages that utilize the taxonomy term “Linux”
Automating Virtual Machine Installation Using libvirt, virsh And cloud-init
Introduction
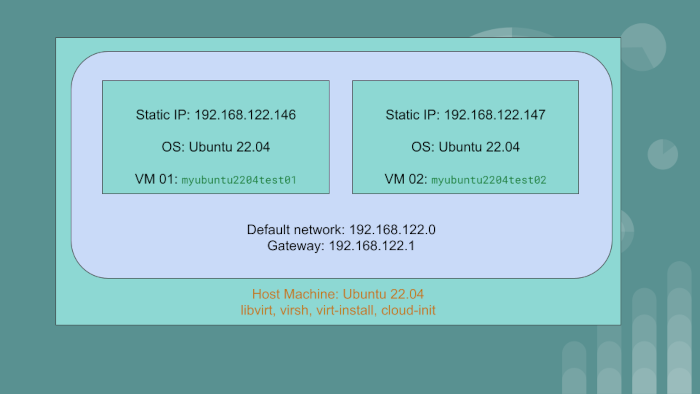
We have the host machine with the OS Ubuntu 22.04. On this PC or server, we will create two virtual machine guests:
myubuntu2204test01having static IP of192.168.122.146myubuntu2204test02having static IP of192.168.122.147
The guest VMs will use the default network created by libvirt. The gateway IP for the default network
is 192.168.122.1.
We will achieve automation using libvirt, qemu and cloud-init. To go through the article and exercise,
you should have a rudimentary understanding of Linux system administration and networking.
Loading SSH Key Into Memory
So, you have an SSH key pair. The public key has been added on to the server. On the client, ie your laptop/desktop you have your private key. For some reason, your private key has not been loaded into memory.
All you have to do is start the ssh-agent and then load the key into memory via ssh-add.
Step 1: Start the agent
eval $(ssh-agent)
Step 2: load the key into memory
Linux KVM Bridge
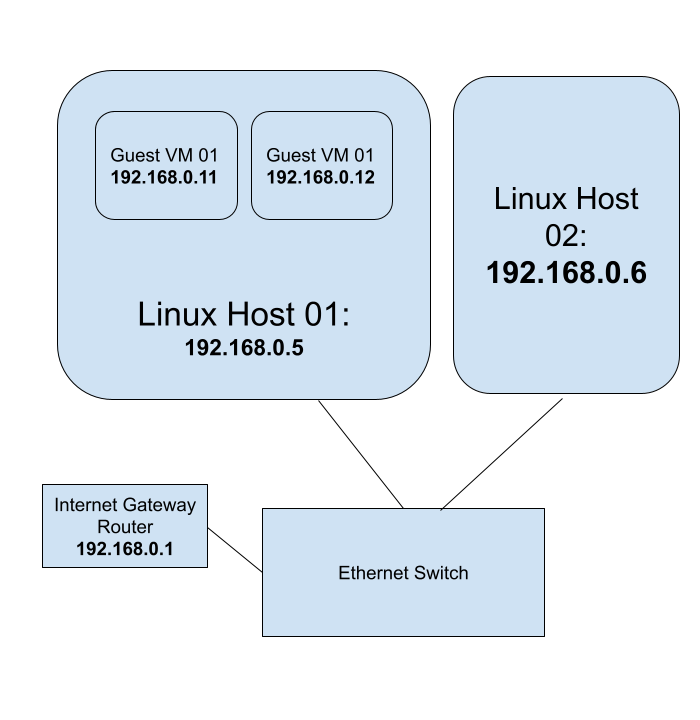
Using Linux KVM, Expose Virtual Guests On The LAN
Audience: The blog post is for beginner to intermediary Linux system administrators.
- You should have a thorough understanding of the shell commands and
- be comfortable on the command line
- be able to install and configure packages, etc.
- be able to start and stop services using
systemd - be familiar with Linux configuration files
- be able to set Linux kernel parameters using
sysctl - be able to enable and disable Kernel modules
- be comfortable installing and using guest VMs using
libvirt
You should have a rudimentary understanding of networking concepts and tooling such as
The Ansible Learning Path
Ansible Prerequisites
Before jumping on to learning Ansible, have a firm grounding in Linux system administration and shell scripting. You can use Ansible for a lot of automation projects. The primary target audience for this blog post are DevOps engineers, IT infrastructure engineers and system administrators who create and manage IT infrastructure to run workloads. A good understanding of YAML is required before starting to write Ansible playbooks. A background in at least one programming language helps. Python programing is not a requirement per se. But Python programming familiarity helps put together some automated testing.
Linux virtualization
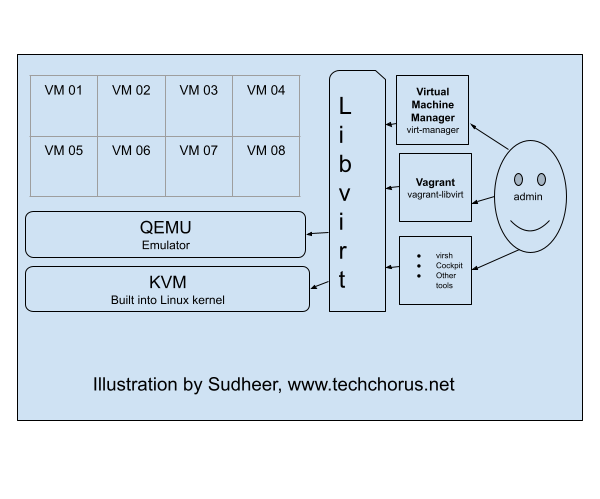
KVM (Kernel-based Virtual Machine), libvirt, and QEMU are three components that work together to provide a
virtualization solution on Linux systems.
KVM is a virtualization infrastructure built into the Linux kernel that allows it to run multiple virtual machines (VMs) on a single physical host. It provides the underlying virtualization technology, such as hardware acceleration for virtualized CPU and memory, and device emulation.
DevOps Lab: Run Your Own File Server
NFS Server
To run your own NFS (Network File System) server, you’ll need to first install Linux on your server. I’d go with
Debian, Ubuntu or CentOS distributions. Once you’ve done that, you can install the NFS server software, which is
typically included with most Linux distributions. After the NFS server software is installed, you’ll need to configure
it to specify which directories on the server should be shared with NFS clients, and what type of access they should
have. This typically involves editing the server’s configuration file, which is typically located at /etc/exports.
Once the server is configured, you can start the NFS server and begin sharing files with NFS clients. To access the
shared files, the NFS clients will need to mount the NFS share using the mount command.
DevOps Lab: Run Your Own Log Server
syslog
Syslog is a standard for logging system events on Unix and Linux systems. It is typically used to collect and store log messages from various applications and system components, such as the kernel, system libraries, and applications. Syslog uses a client-server model, where each client application sends log messages to a central syslog server, which then stores the messages in a log file. The syslog server can also forward the log messages to other syslog servers or send them to a log management system for further analysis. Syslog uses a simple text-based format for its log messages, which makes it easy to read and analyze. It also supports multiple levels of severity, allowing applications to categorize their log messages based on importance.
DevOps Lab: Run Your Own Monitoring Server
There are many tools and software programs that can be used for monitoring and performance analysis on Linux systems. Some popular options include:
- top - This is a command-line utility that shows real-time information about the processes running on a Linux system, such as their CPU and memory usage.
- htop - This is a more advanced version of top that provides a more user-friendly interface and additional features, such as the ability to sort processes by different metrics and to kill processes.
- sar - This is a command-line utility that collects and displays performance metrics for a Linux system over time. It can be used to analyze CPU, memory, I/O, and network usage, as well as other metrics.
- iostat - This is a command-line utility that shows real-time information about I/O performance on a Linux system. It can be used to monitor the performance of disks and other storage devices.
- vmstat - This is a command-line utility that shows real-time information about various system resources, such as memory, CPU, and I/O. It can be used to monitor the overall health of a Linux system.
- netstat - This is a command-line utility that shows information about network connections on a Linux system. It can be used to monitor the status of network connections and to diagnose networking issues.
There are also many modern monitoring tools and software programs available for Linux, such as Prometheus and Zabbix. These tools typically offer more advanced features and capabilities than the built-in Linux utilities, such as the ability to collect and store metrics over time, and to generate alerts when certain conditions are met.
Learning Linux For DevOps
Introduction
If you have chosen the DevOps engineering path for your career, Linux system administration skills are a must. Companies run their workloads on Linux on-premise as well as in the cloud. Many developers write software on their Linux laptops and workstations. In this post, I will lay out a plan to master Linux system administration skills. The journey begins with you becoming a Linux desktop user. Gradually, you start using your laptop as a Linux server. Become more productive and create your own labs using virtualization. You will be able to simulate a lot of Linux infrastructure scenarios on your laptop.
Sysctl
Introduction
The Linux Kernel parameters are settings that can be configured to control the behavior of the Linux kernel. They are typically used to fine-tune system performance or to enable/disable certain features.
Some examples of kernel parameters include:
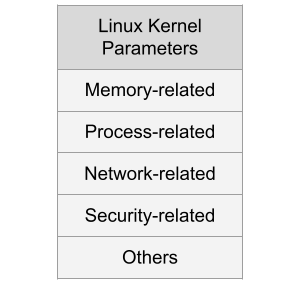
Memory-related parameters: These parameters control how the kernel manages system memory, including how much memory is allocated to user processes and how aggressively the kernel caches data.
Processor-related parameters: These parameters control how the kernel interacts with the system’s processors, including how it schedules processes and how it handles interrupts.
Map SSH Keys To Git Projects
Using Git with SSH is a common practice among software developers. The convenience of not having to remember passwords is a huge productivity boost in software development workflows.
In a previous blog post, I wrote about managing SSH keys.

Having many SSH keys can cause few issues:
ssh-agentdoesn’t work well with too many keys.- Can’t always map SSH keys to servers in SSH client configuration. Both personal and company projects Git can be hosted on the same server or third-party service such as Github.
- Some Git hosting services do not allow you to use the same SSH key in more than one user profile. You are forced to have a unique SSH keypair per user profile.
- The SSH server might refuse to allow too many authentication attempts.
Git allows you to set the environment variable GIT_SSH_COMMAND. If you set this environment variable, Git uses the
specified command for push and pull operations.
SSH Key Management
What is SSH Key Management?
The blog post is intended towards someone new to SSH key management. Do you have just one SSH key pair? Do you have multiple key pairs? What are some pros and cons of having single or multiple key pairs? The post answers such questions about SSH key usage in practice.
The Premise
So, someone walked up to you or in a video call asked for your SSH public key?
Run Your Own OpenVPN Server
Introduction
The article explains how to run your own OpenVPN server. We will create a Certificate Authority Server and an OpenVPN server. We will also generate certificates for the clients. We will also learn how to manage revocation of client certificates using the Ansible roles.
Use the Ansible roles gavika.openvpn and gavika.easy_rsa to install and configure your OpenVPN server.
You can install the OpenVPN server on any public cloud or hosting provider or on-premise servers. The Ansible roles
are designed to install the OpenVPN server and a Certificate Authority server.
Creating Administrative Linux User Accounts: gavika.administrators
We are pleased to announce gavika.administrators.
The Ansible role provides a declarative method to create Linux
user accounts with administrative privileges. In other words, these users have sudo access without password and are
empowered to run all commands on the system.
You might be wondering why you would need a role when you can write a couple tasks yourselves in an Ansible playbook. The reason is, Do Not Repeat Yourself(DRY). Instead of writing such tasks over and over, use the abstraction provided by the role. You just have to write some YAML declaration and be done with it. Moreover, the maintenance is outsourced to an Apache licensed open source software. The role has Molecule tests to boost your confidence.
Gavika Ansible Roles
Yesterday, we announced the launch of Ansible role to install and configure AWS CloudWatch Agent.
You might have seen my other open source Ansible roles on Ansible Galaxy and Github.
In the same spirit, the company, Gavika Information Technologies Pvt. Ltd. Bangalore, has started publishing open
source projects on Github.
Ansible role to install and configure AWS CloudWatch Agent
is the first project. Expect more projects in the future.
These are some guidelines for the Ansible role projects that Gavika follows:
Simple Password Vault With Ansible
Ansible comes with a vault feature. It is meant to be used in the context of configuration management. But you can also use it as a standalone simple password vault for your personal or organization’s use.
Initial setup of password vault:
- Create or clone a Git or another SCM repository
git init
- Create the password vault
ansible-vault create myvault.secret
Type the new master password and confirm, ansible-vault will open your text editor. Type your secrets in the editor and save and quit. To open your vault for viewing or editing in the future, you will need your vault password.
Understanding and Implementing MySQL Replication: A Guide for All Skill Levels
In this tutorial, I will provide step-by-step process to implement MySQL replication. We will create one master and one slave. We will use two CentOS 6 servers - one for master and the other for slave. This following steps have been tested on two virtual machines.
Our master server will have IP address 192.168.122.10. Our slave server will have IP address 192.168.122.12.
You might want to run SELinux in permissive mode.
Becoming Productive In Bash Using The Keyboard Shortcuts
Moving around
You can use the arrow keys on keyboard to move around in the command line. Bash also provides convenient keyboard shortcuts to navigate effectively. Try them out and see for yourself.
To become a Bash pro user you have to get yourself familiar with the keyboard shortcuts. Once you do, you’ll find yourself productive.
| Shortcut | Description |
|---|---|
| CTRL+b | move backward one character |
| CTRL+f | move forward one character |
| ESC+b | move one word backward |
| ESC+f | move one word forward |
| CTRL+a | move to beginning of line |
| CTRL+e | move to end of line |
| CTRL+p | move to previous line |
| CTRL+n | move to next line |
| ESC+< | move to first line of history list |
| ESC+> | move to last line of history list |
Moving around words using ESC+f and ESC+b are my favourites in this list. Jumping to first and last lines of the
history list is also useful.